Industry Insights at 7Clouds® Stay Connected with Industry Trends, Tips and News
DNS Security – A Brief Overview of DNSSEC

DNS offers an easy way to identify internet and private network-connected resources. With vulnerabilities in authenticity verifications, however, security is a concern. That’s where DNSSEC comes in.
What is DNS?
The Domain Name System (DNS) uses domain names as user-friendly identifiers for computer-friendly IP addresses. For example, the www.7Clouds.com domain name translates to a specific IP address, but both the name and the IP address identify the same website. The domain name is simply easier to remember and use.
A domain name and associated DNS data is sorted and stored onto name servers, which a user/device uses to look up this data. This process is called DNS name resolution.
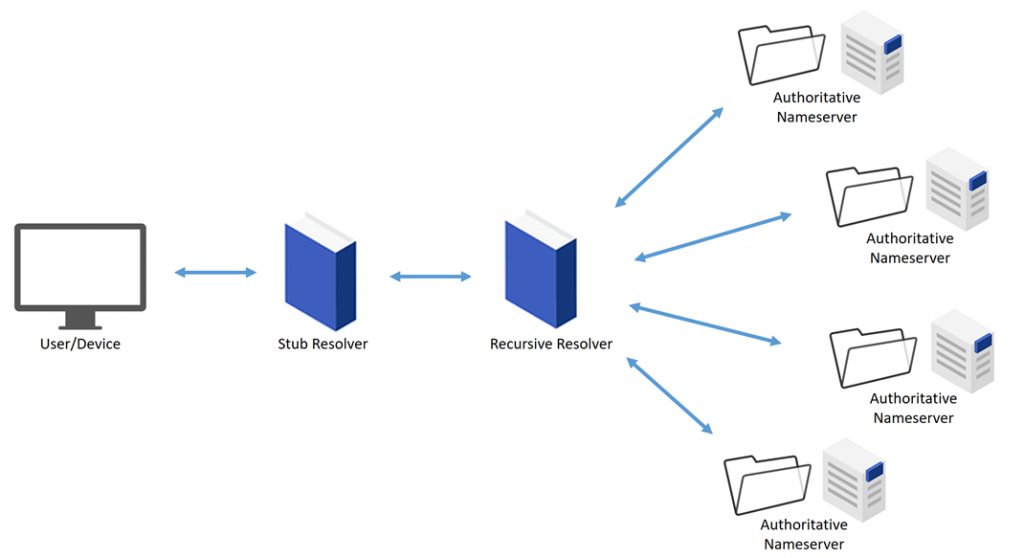
The above-illustrated resolution process begins with a command from a device, such as a user sign-in. This command is sent to the stub resolver, which is a part of the device’s operating system, thereby beginning the translation of a domain name to an IP address. The stub resolver then sends a query to the recursive resolver, which sends its own queries to multiple nameservers in order to respond to the stub resolver and, in turn, the user/device command.
DNS structure is organized into zones, which then subdivide into “child” zones. These child zones must have the necessary data to refer to other NDS servers, allowing a user to find the domains within the parent zone. In other words, every parent zone must hold nameserver records for each of its child zones.
DNS, though a crucial component of web operations, does come with its vulnerabilities.
DNS security concerns
Cause for concern in DNS security often comes down to authenticity verification. When the recursive resolver sends its query to the nameserver, it cannot verify the authenticity of the response; it can only confirm whether the IP address that the response came from is in fact the same IP address to which it sent the query. As a result, if the source IP address is altered by attackers, a response can appear as though it came from the desired nameserver, leading unsuspecting users to malicious sites.
Recursive resolvers can also cache DNS data from nameservers. This way, when a stub resolver asks for data the recursive resolver has cached, the recursive resolver doesn’t need to send queries to the nameserver again, speeding up the overall resolving process. Though efficient, this means that an attacker who has manipulated a DNS response can easily poison this cache if the response is accepted by the recursive resolver. With the fraudulent DNS data cached, the recursive resolver will continue to send it to the devices that query for it.
To overcome these security vulnerabilities, DNSSEC can be enabled.
DNSSEC: The DNS security extension
With DNSSEC, DNS data is signed by the zone owner. This digital signature acts as a private key which allows resolvers to verify that the data has not been modified before transmitting it to the user. If the data has been altered in any way, the user will not receive the desired response from the resolver, thereby mitigating any threat.
Each zone also has a public key, visible to anyone in the zone itself. When a user makes a data request, the recursive resolver receives this public key to verify that the data actually comes from the intended zone. If this signature can’t be verified, the resolver sends an error message to the user, rather than the requested data.
This added security and validation stretches beyond the zone to its parent and root zone. Simply put, a zone’s public key is always signed by its parent zone (for example, the org zone of a .org domain), until the root zone is reached, which has no parent to sign its public key. As a result, a resolver that trusts a root zone’s public key can trust the public key of any zone’s signed, or authenticated, by the root zone. These authenticated zones go on to sign public keys of child zones, creating a chain of trust and security organizations rely on to keep their networks safe.
7Clouds - Contact us today to learn more about DNSSEC and how our managed services can keep your business networks safe and efficient.

References
ICANN, DNSSEC – What is it and Why is it Important? 2020.
ARIN, Securing DNS (DNSSEC). 2020.
Images: Pixabay
Tags
Latest Posts
Popular Posts
-
From SMEs to Families: Enterprise Virtualization Tips for Confinement with the Kids
From virtual machines to virtual workplaces, SME virtualization technology is securing its place in the family household as COVID-19 keeps us home. The shift towards...
-
7Clouds® Managed Services Yield Results
7CLOUDS Managed Services Yield ResultsDownload





Stay Connected With Industry Trends & News
Sign Up for Our Newsletter

