Industry Insights at 7Clouds® Stay Connected with Industry Trends, Tips and News
Network Security FAQs: VPN Top Picks

IBM's 2019 Cost of Data Breach Report pinned the average international cost of a business data breach at USD 3.92 million, with the most fiscally affected country being the United States at USD 8.19 million. Large-scale network and data breaches affect more businesses now than ever, shining a light on VPNs and network security. So, what are some top VPN FAQs?
VPN vs. Proxy – What’s the difference?
Both VPNs and Proxies allow users to access the internet by first connecting to a server at another location. This can make it appear as though a user is accessing the internet from an IP address that’s not their own, for example, or can be useful in applying corporate network use policy and web traffic monitoring for the many users within an enterprise. How the two services achieve these tasks is where they differ.
A proxy is applied at the application level. It can relay either only web traffic (HTTP, HTTPS) or traffic from several different applications at once (SOCKS). HTTP proxies are seldom used today, as HTTPS proxies offer more security and privacy with an encrypted connection between the web server and a user’s web browser. In addition, Proxy servers can build up a pool of IP addresses which applications can use to access the internet.
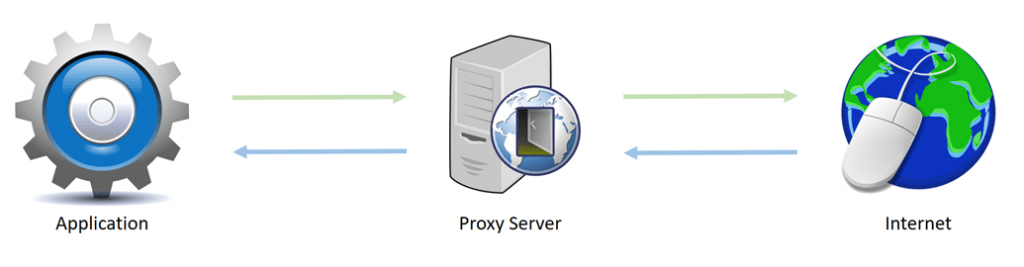
VPNs are applied at the device level, acting on a device network as a whole, rather than the connection of individual apps. They provide an encrypted tunnel for traffic between users and the VPN server, offering the security and the scale for larger tasks, such as uniting all corporate users onto one server, particularly when paired with a firewall and email security appliance.
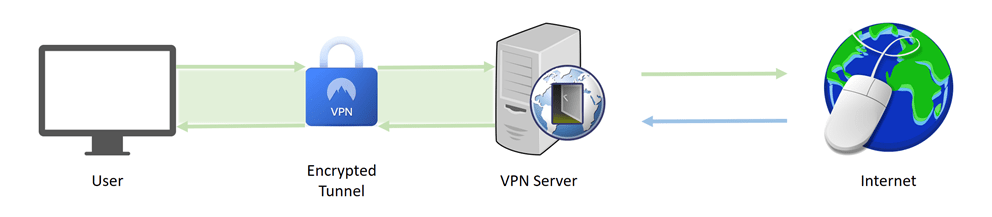
Deciding when proxy or VPN use is best, or how to optimally combine the two is a matter of scale, cost and security.
What kind of maintenance does a VPN need?
Key to VPN maintenance for businesses is the consistency of updates. Generally, a VPN provider will make updates available as soon as changes have been applied. Some providers make these updates mandatory for further use of the VPN – getting them out of the way immediately -, while others allow the user to schedule an update. In either case, installing updates as they become available – keeping your VPN up to date – is critical.
Businesses should also remain vigilant of current cybersecurity alerts. The Cybersecurity and Infrastructure Security Agency (CISA), for instance, releases warnings such as the recent Alert (AA20-010A) for the Continued Exploitation of Pulse Secure VPN Vulnerability, in which a remote code execution (RCE) vulnerability (CVE-2019-11510) was exposed as a target for attacks exploiting unpatched Pulse Secure VPNs. Keeping an eye out for alerts like these, as well as following through with the appropriate updates, reduces the response time to and severity of cybersecurity issues and attacks.
Are VPNs safe?
With a trustworthy provider, VPNs are safe, allowing for secure internet access. To assess whether a VPN service provider is trustworthy, it’s important to know the user agreement – well. Some providers collect user data, such as connection tendencies and IP addresses, defeating the purpose of VPN use for any privacy concerns. The user agreement identifies the data collection practices of the provider and is the first reference in selecting the right provider.
Typically, the less a VPN provider logs, the better for your privacy and security. Beyond the user agreement, businesses should be aware of a provider’s location (country) in order to understand any associated data retention laws, for example. Different jurisdictions might also require different types of information to be made available in the user agreement, making it important to detect any potential omissions. Just as in VPN maintenance, It comes down to vigilance.
7Clouds - Contact us today to discuss how our filly secured VPN service with entry-point threat mitigation and traffic control can meet the security requirement of your business.

References
CISA, Alert (AA20-010A): Continued Exploitation of Pulse Secure VPN Vulnerability. January 2020.
NIST – NVD, CVE-2019-11510 Detail. October 2019.
IBM, 2019 Cost of Data Breach Report highlights. 2019.
Images: Pixabay
Tags
Latest Posts
Popular Posts
-
From SMEs to Families: Enterprise Virtualization Tips for Confinement with the Kids
From virtual machines to virtual workplaces, SME virtualization technology is securing its place in the family household as COVID-19 keeps us home. The shift towards...
-
7Clouds® Managed Services Yield Results
7CLOUDS Managed Services Yield ResultsDownload





Stay Connected With Industry Trends & News
Sign Up for Our Newsletter

