Industry Insights at 7Clouds® Stay Connected with Industry Trends, Tips and News
Secure VPN Service: Threat Protection into the Unknown

We often hear about how VPNs can protect our information, location, and identity from the internet – but then what? Beyond that secured tunnel are threats to which users and enterprises remain vulnerable without adequate protection. Filtering traffic at this level protects enterprises from these threats, ensuring a fully secure VPN service.
What is a VPN?
The use of a VPN (Virtual Private Network) routes user data to/from the internet through servers at another location. This makes data from the user appear as though it’s coming from a server operated by a VPN provider. For VPNs that encrypt data, this also means protecting data from being read by anyone monitoring the network connection. The following diagram demonstrates a basic VPN pathway.
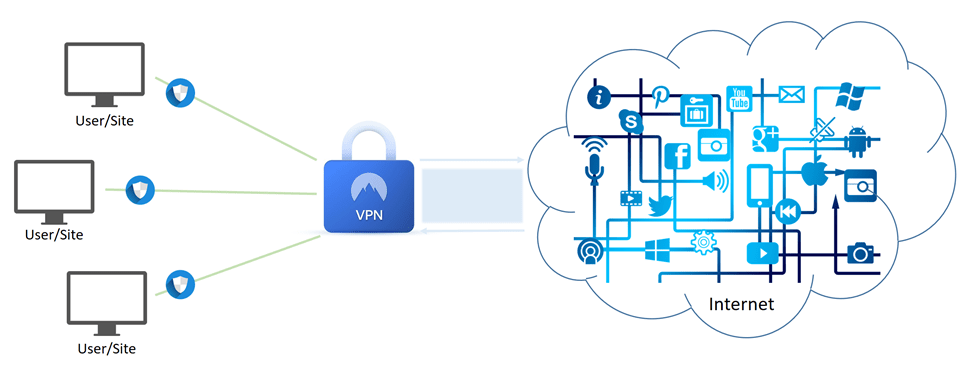
Simply put, the use of a VPN to access the internet provides a secure, encrypted tunnel (shown in green above) for data to and from a user. But, what happens after data leaves that secure tunnel?
A shift in focus
The security of a VPN is focused between the user and the VPN server. Beyond this server, to the internet, the connection loses this security and data remains vulnerable. Any threats picked up on the internet can then potentially be brought back to the user through an open VPN tunnel.
With sufficient security (firewall, antivirus…), the user is protected. But, what if that protection were applied at the VPN level? Shown below, by shifting security focus one step back, to the server, threats can be blocked before they are ever able to infiltrate a corporate network, for example.
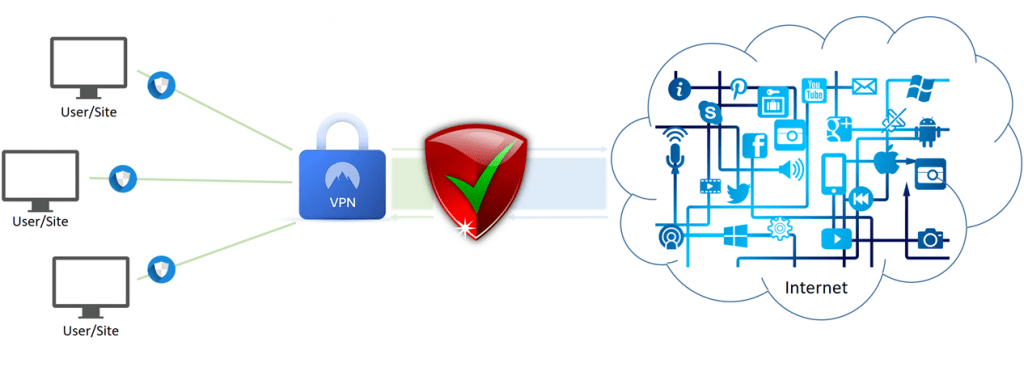
Monitoring traffic from the internet into and out of a secure VPN tunnel allows security processes to block threats at the earliest point of entry. As a result, the security of VPNs shifts from identity and location masking to threat protection and mitigation. At this level, it’s about which adaptive security appliance offers the best protection for your security needs.
VPN and enterprise security services
When it comes to threat protection, firewall and email security are key. The right firewall appliance efficiently filters data on route to and from the internet, while an email and spam security appliance keeps communications clean.
Placing these appliances (or filters) at the VPN level offers advantages user-to-user, as well as for larger enterprises. Users and smaller businesses, for instance, may opt for a full VPN security package, allowing for more simplicity and less investment in on-site protection services and infrastructure. Larger enterprises, on the other hand, can use the approach to manage the security of several sites simultaneously, early on in the network infrastructure. In either case, efficient network security services must offer the ability to adapt and grow with network changes.
7Clouds - Contact us today to discuss how our filly secured VPN service with entry-point threat mitigation and traffic control can meet the security requirement of your business.

Reference
Federal Trade Commission, Virtual Private Network (VPN) apps. March 2018.
Images: Pixabay
Tags
Latest Posts
Popular Posts
-
From SMEs to Families: Enterprise Virtualization Tips for Confinement with the Kids
From virtual machines to virtual workplaces, SME virtualization technology is securing its place in the family household as COVID-19 keeps us home. The shift towards...
-
7Clouds® Managed Services Yield Results
7CLOUDS Managed Services Yield ResultsDownload





Stay Connected With Industry Trends & News
Sign Up for Our Newsletter

